Traditionally focused on mitigating the effects of malicious cyber attacks, such as those experienced in the Change Healthcare and MOVEit incidents, the industry is now turning its attention to IT system failures as a critical source of systemic risk. Sectors like aviation, which are particularly susceptible, have been especially affected by this non-malicious event.
Accelerated Product Innovation
In response to the outage’s unique characteristics, the cyber insurance market is set to drive innovation on two key fronts. Firstly, there is anticipated growth in the development of new insurance products designed to address downtime risks associated with IT failures.

Parametric insurance products, which offer quick payouts based on predefined triggers, are expected to gain prominence. While these products were already in development, the increased risk awareness is likely to expedite their introduction to the market.
Secondly, the industry is expected to refine its definitions and categorisations of systemic events. This includes updating how various types of cyber incidents, including non-malicious failures, are classified by severity. Initiatives such as the UK’s newly established Cyber Monitoring Centre, launched earlier in 2024, will support these efforts, aiding insurers in creating products for newly identified risks.
These advancements underscore the importance of obtaining high-quality broking advice to secure the most effective and cost-efficient coverage amidst an evolving risk landscape.
Rising Demand Amidst Increased Awareness
The outage has also heightened global awareness of cyber risks, which is expected to drive increased demand for cyber insurance. According to Microsoft, the outage affected 8.5 million Windows devices, demonstrating the extensive impact of such incidents.
Howden’s recently released analysis projects that over half (54%) of the growth in cyber premiums through 2030 will come from markets outside the US, with 25% of the growth occurring in continental Europe. This expansion reflects the growing recognition of cyber insurance as essential for enhancing resilience against digital threats.
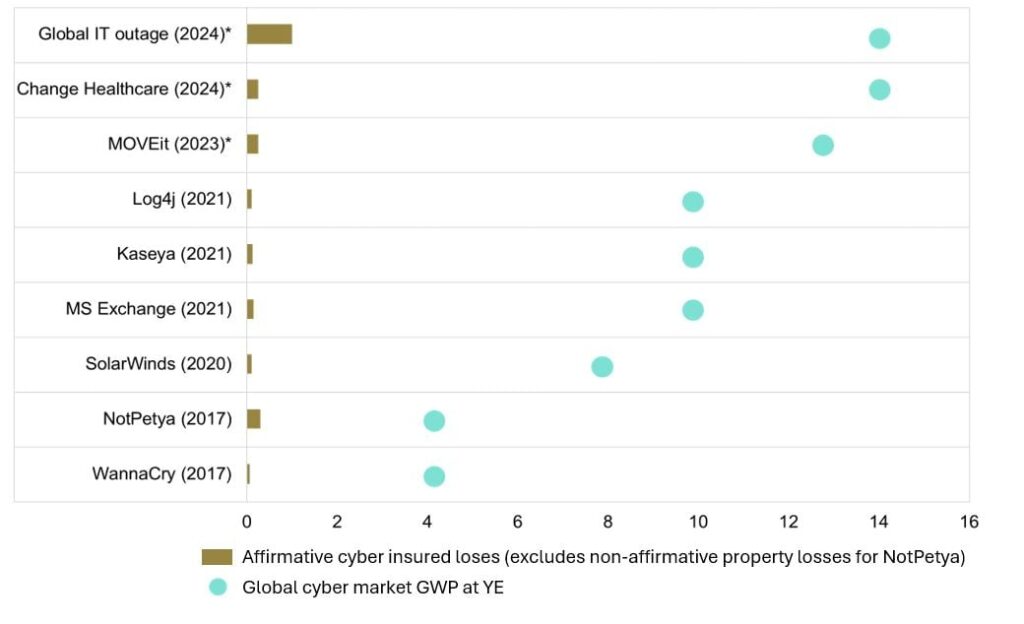
Source: Howden, PCS, Barclays, Parametrix, CyberCube
Moreover, research from the World Economic Forum highlights a significant protection gap among small and medium-sized enterprises (SMEs). Organisations with revenues under $250 million are, according to their data, three times less likely to have cyber insurance compared to those with revenues over $5.5 billion.
The gap is concerning given SMEs’ limited IT expertise and resources, which makes them more vulnerable to major cyber events.
Cyber Insurtechs Focus on Customer Clean-ups
Coalition, a leading US-based cyber insurtech which was unaffected by the outage, has spent the days since the attack tackling customer claims via their response teams. The company said that in the wake of the CrowdStrike outage, many policyholders are seeking clarity on coverage – but the answer varies depending on several factors, including the nature of the incident, the affected entities, and specific policy terms.
A statement released by Coalition’s CEO, Joshua Motta details the company’s own challenges, and the wider industry, saying that most cyber insurance policies, including Coalition’s, cover certain business interruption events. This typically includes compensation for lost income and additional expenses, such as overtime and extra IT resources needed for recovery.
The fallout from this event illustrates the very real public policy tension that exists between the benefits of economies of scale and the risks associated with concentration.
Joshua Motta
Motta notes that the hype surrounding the event has also sensationalised the perception of loss, which according to all indications, is currently not comparable to the losses incurred through natural disasters by the insurance industry.
He says: ”...despite the media hysteria and significant impact of these events, including the CrowdStrike outage, which has been called “the largest IT outage in human history,” we do not expect any to reach the levels of loss of natural catastrophe events that routinely impact the insurance industry.
“Our own modelling, leveraging our Active Cyber Risk Model, suggests a $0.96 billion industry-wide loss experienced by US cyber insurance policyholders at the upper bound prior to consideration of coverage limitations. Of course, any model of this event will also be highly sensitive to the least credible assumption (most likely, the share of impacted systems), which if reduced, would decrease our estimate to $0.27 billion (or lower).”
A Call for Caution and New Processes
Rory Yates, Global Head of Strategy at EIS, says the industry should view the incident as a learning opportunity. He urges leaders to adopt sensible caution, risk mitigation, and new processes to better manage future risks. The CrowdStrike outage serves as a crucial moment for technology providers and their clients to refine their approaches and avoid significant losses in the future.
He also believes that while the CrowdStrike outage was similar to a serious cyber incident in its overall impact, it’s important to emphasise that it wasn’t one – and as such, the implications, risks, and the process of recovery are “therefore much different”.
“CrowdStrike quickly put a fix in place, but the knock-on effects had already kicked in, taking down machines and overloading cloud infrastructure,” Yates says.
“Disruptions were felt in critical sectors such as healthcare, retail, financial services, and hospitality. Thousands of flights were cancelled, costing £millions in lost revenue. There were also bizarre impacts. It’s been reported that it shut down 30% of McDonald’s stores in Japan.”
Lessons Need to be Learned
He notes that because insurers have carefully considered the implications of this event and are continuing to support their clients with largely unchanged coverage, “this implies a greater resiliency in the cyber insurance market than some would have imagined.”
He also points out that the event has also highlighted the fragility of the internet’s general infrastructure, the deep interconnectedness of services, and the gamut of unexpected threats is larger than many expected.
“For insurance, this is a crucial insight. The CrowdStrike outage highlighted significant catastrophic risks in digital supply chain interconnectedness. This not only disrupted CrowdStrike’s customers but also propagated through third-party networks, impacting the resilience of seemingly unrelated industries.
“As people rebuilt systems, or as certain systems were offline, it’s very likely malicious actors attempted to target potential vulnerabilities. We now know that bad actors were out in force following the outage, executing phishing attacks, and scam-calling impacted businesses.”
Legacy Systems Increase the Likelihood of Damage
Insurers relying on outdated or semi-modern core systems are also essentially risking their business continuity, Yates said, noting that this holds true whether these systems have been moved to the cloud or are still dependent on centralised server infrastructure.
The CrowdStrike outage highlighted significant catastrophic risks in digital supply chain interconnectedness. This not only disrupted CrowdStrike’s customers but also propagated through third-party networks, impacting the resilience of seemingly unrelated industries.
Rory Yates
The main issue is that systems merely labelled as “cloud-based” are typically migrated to a single public cloud provider—such as AWS, Microsoft Azure, or Google Cloud. If that cloud provider experiences downtime, the entire system is affected, and all critical operations it supports come to a standstill.”
Yates explains: “The system vendor can give the affected customer the base code to redeploy the system, but full recovery from the ground-up takes six to nine months. Meanwhile, the business losses an insurer undergoes might be fatal. This is no better than what you’d deal with post-outage if you had a fully on-premises core infrastructure.
“CrowdStrike announced measures to mitigate the risk of future disruptions, but the outage should serve as an important moment for all technology providers and their clients.”
Changes to the Cyber Insurance Market
Motta concludes that across the cyber insurance market, especially among those with more limited resources, it’s anticipated that concerns will increasingly be managed by altering, restricting, or excluding coverage.
Some insurers have already implemented sub-limits for catastrophic or widespread losses, which might restrict or exclude coverage for cyber incidents affecting numerous organisations. Others are introducing sub-limits for dependent or contingent business interruptions, applying exclusionary terms to entities that were not direct targets but still suffer due to supply chain cyberattacks, or even removing coverage altogether, potentially on a temporary basis.
He writes: “Undoubtedly, this will continue to be a topic of great interest for (re)insurers, regulators, and the broader cybersecurity community as a mere fifteen companies worldwide account for 62% of the market for cybersecurity products and services. The fallout from this event illustrates the very real public policy tension that exists between the benefits of economies of scale and the risks associated with concentration. We also expect that impacted companies and their insurers will pursue indemnification from CrowdStrike, whose liability remains to be determined.”
Yates adds: “We must view this as a huge learning opportunity. Each market loss related to these events, especially headline-grabbing and well-publicised one, grows our understanding of nuances in quantifying cyber exposure and systemic threats while testing the efficacy of coverage and relevancy of the products.
“What we need to do now is see sensible caution, risk mitigation, and new processes put in place. Otherwise, we’ll be talking about doomsday loss quantums and throwing a lot of the benefits out with the trash.”
Reporting by Joanna England










